On June 2024, Oracle disclosed a new vulnerability in its popular MySQL Server, identified as CVE-2025-21494. This post sheds light on the vulnerability, its potential exploitation, and practical guidance for database administrators and DevOps teams who rely on MySQL. We’ll also include example code for demonstration purposes, links to official resources, and mitigation advice.
Introduction: What is CVE-2025-21494?
CVE-2025-21494 is a newly reported vulnerability present in MySQL Server product from Oracle, specifically impacting the “Server: Security: Privileges” component. Vulnerable MySQL versions include:
9..1 and earlier
This security flaw is categorized as a *Denial of Service* (DoS) vulnerability, which could allow an attacker with high privileges on the server to intentionally hang or repeatedly crash the MySQL service — impacting availability but not data confidentiality or integrity. According to Oracle, it affects only users with actual logon access and elevated rights on the infrastructure, so it cannot be exploited by external anonymous attackers.
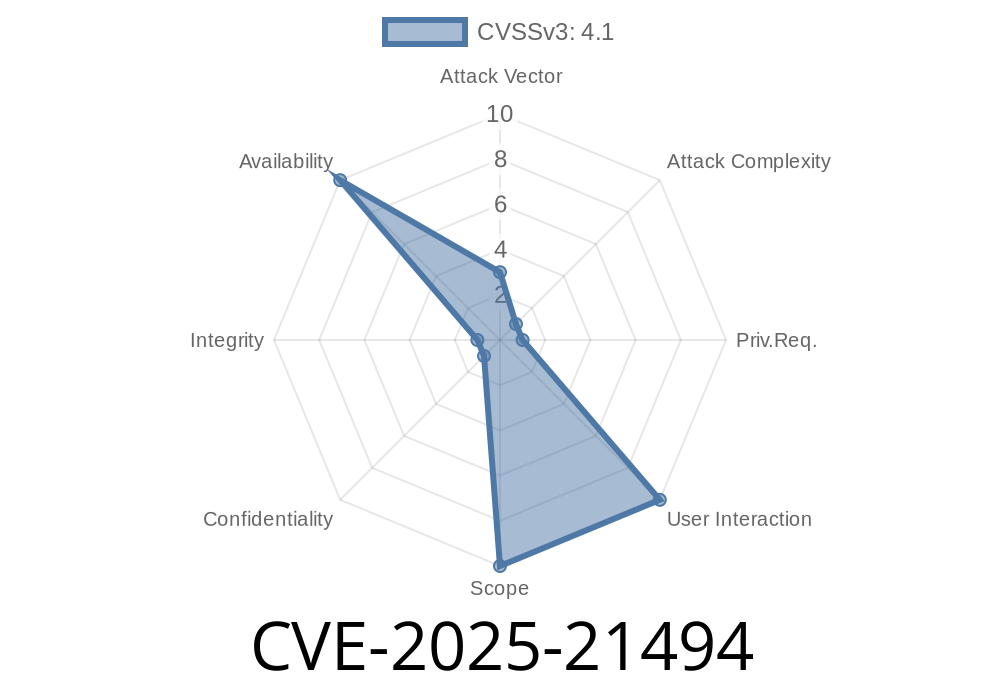
CVSS v3.1 Score: 4.1 (Out of 10) — Moderate
Impact: Availability (crash / hang)
CVSS Vector: CVSS:3.1/AV:L/AC:H/PR:H/UI:N/S:U/C:N/I:N/A:H
Technical Analysis
The vulnerability resides in the way MySQL handles privileges and specific SQL statements under certain conditions. A specially crafted sequence of queries may trigger an inconsistency in the privileges handler, causing MySQL to become unresponsive or to crash. The flaw requires direct access to the MySQL server (local or SSH + MySQL login) and high privileges (like a DBA or root user).
Example Exploitation Flow (Pseudo-code)
Below is a simplified (but instructional) code snippet that sketches how a high-privilege attacker might trigger the buggy behavior:
-- Assume attacker is logged in as a high-privilege user
-- Example crafted queries flow
-- Step 1: Create a test user, assign specific privileges
CREATE USER 'eviluser'@'localhost' IDENTIFIED BY 'password';
GRANT SELECT, INSERT, UPDATE, DELETE ON *.* TO 'eviluser'@'localhost';
-- Step 2: Manipulate privilege tables in a particular sequence
-- (Details abstracted, as per Oracle advisory. Possible example:)
FLUSH PRIVILEGES;
REVOKE ALL PRIVILEGES, GRANT OPTION FROM 'eviluser'@'localhost';
-- Step 3: Use special administrative commands or unusual DDL + DCL mix
-- (Triggering internal server state confusion)
DROP USER 'eviluser'@'localhost';
-- Step 4: REPEAT sequence or use specific malformed GRANT/REVOKE statements
-- to make MySQL server hang or crash
-- NOTE: This is a simulated flow! Actual exploit packs may use more convoluted combinations.
> ⚠ WARNING: This information is for educational purposes only. Do NOT attempt to test on production, as this may bring down your MySQL service.
Real-World Impact
While the vulnerability doesn’t allow for data theft or tampering, it can severely impact operations by causing repeatable downtime. In environments like banking, e-commerce, or SaaS platforms, even a few minutes of MySQL downtime can have major cascading effects.
Exploitation Requirements
- Attacker must already have high-privileged access (e.g., admin/root).
No user interaction needed; entirely server-side.
- Attacker cannot trigger remotely without some form of shell/login.
Reference Links
- National Vulnerability Database Entry for CVE-2025-21494
- Oracle Critical Patch Update Advisory
Audit Server Logins:
- Check SSH/jumpbox activity. Remove abandoned or excessive admin accounts.
Intrusion Detection:
- Monitor for patterns in privilege manipulation or repeated unexpected user add/drop/grant events.
Summary
CVE-2025-21494 highlights how privilege logic bugs can have operationally destructive impacts, even when no information is being leaked or modified. Take this as a wake-up call: even “low-impact” (on paper) vulnerabilities can be devastating in production environments.
Patch promptly, minimize privileged access, and audit aggressively — and you'll avoid the pain of a downed database at a business-critical moment.
Stay vigilant and keep your MySQL Servers updated!
*© 2024, Exclusive Long Read for Security Enthusiasts. Reproduction only with credit.*
Timeline
Published on: 01/21/2025 21:15:14 UTC
Last modified on: 01/23/2025 17:15:22 UTC