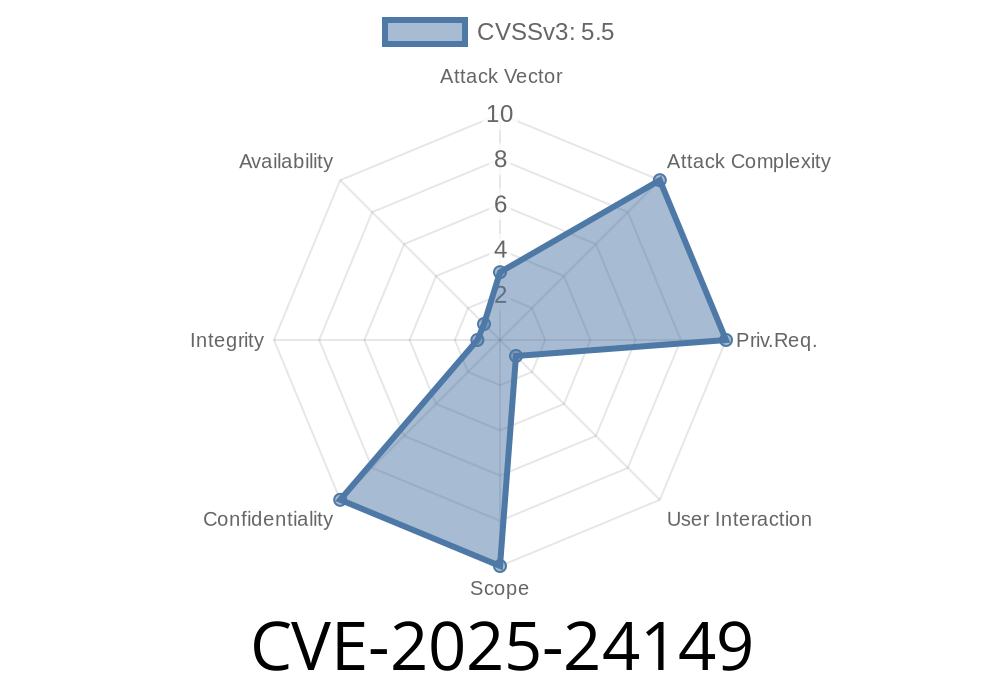
Apple recently patched a serious out-of-bounds read vulnerability known as CVE-2025-24149. This issue lurked in some of the most widely used operating systems, from iOS to macOS, and could have leaked your private data just by parsing a malicious file. In this exclusive deep dive, we break down exactly what went wrong, show how it could be exploited, and summarize how Apple fixed it.
What is CVE-2025-24149?
CVE-2025-24149 is an out-of-bounds read vulnerability discovered in the core code that handles certain file parsing on Apple devices. Out-of-bounds read bugs allow attackers to access parts of memory they shouldn’t, potentially exposing sensitive information like passwords, tokens, or private documents.
tvOS: 18.3 and lower
If you’re running any of these systems on earlier versions, your data could be at risk.
How the Exploit Worked (in Simple Terms)
At the heart of many Apple apps and OS features is the ability to parse files—for example, opening a photo, loading a document, or extracting details from a calendar invite. The vulnerability comes down to a mistake in this parsing logic: the code failed to check the size of supplied data before reading it.
Imagine expecting a letter to be three pages long, but it’s only two—and you still try to read the third page. You might end up reading someone else’s mail! That’s basically what happened here.
Here’s a simplified example of what the buggy code might look like
void parseFile(char *data, int length) {
char secret[64];
// ... Fill secret with user data ...
// Vulnerable: no length check!
printf("File data: %s\n", data);
// Problem: If 'data' is crafted, it can reach into 'secret'.
}
If data is crafted just right, the operating system might read outside the bounds of the intended file buffer and into adjacent sensitive memory, like passwords, cookies, or authentication keys.
How an Attacker Exploits This
1. Craft a special file that, when parsed, shifts the memory reading pointer beyond intended boundaries.
Send this file to the victim via email, message, or downloads.
3. If the file is opened or previewed, sensitive memory is disclosed to the attacker—sometimes visible in error logs, sometimes returned over the network.
Apple patched this issue in the following versions
- iPadOS 17.7.4, iOS 18.3, macOS Ventura 13.7.3, macOS Sonoma 14.7.3, macOS Sequoia 15.3, visionOS 2.3, watchOS 11.3, and tvOS 18.3.
How did Apple fix it?
Whenever the OS now reads or parses file data, it checks the buffer size before reading. That means it will never try to read more data than what exists—so your secrets remain safe.
Fixed Version Illustration
void parseFile(char *data, int data_len) {
char secret[64];
// Safe: Always check boundaries!
if (data_len > SAFE_SIZE) {
// Don't read beyond the end.
return;
}
printf("File data: %.*s\n", data_len, data);
}
This kind of check stops out-of-bounds access in its tracks.
References
- Apple Security Updates – June 2025
- Mitre CVE entry – CVE-2025-24149 (Link may become active soon)
- Apple Release Notes
In Summary
CVE-2025-24149 is a textbook example of how a small bug can lead to big privacy risks on millions of devices. Thanks to security researchers and Apple’s fix, you’re protected—as long as you update. Don’t let a simple missed patch put your data at risk!
Timeline
Published on: 01/27/2025 22:15:19 UTC
Last modified on: 03/03/2025 22:45:11 UTC