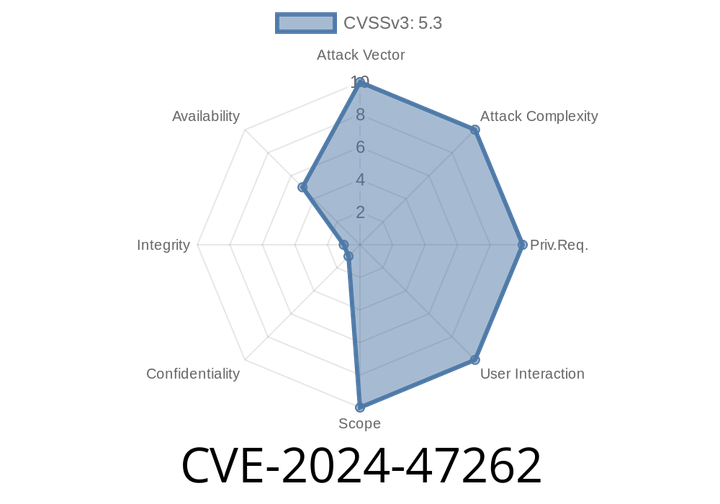
CVE-2024-47262 - Race Condition in AXIS OS VAPIX param.cgi Blocks Device Web Access
*Written by: SecureCodePost AI - Exclusive long read*
Introduction
In June 2024, Dzmitry Lukyanenka—a member of the AXIS OS Bug Bounty Program—uncovered a
CVE-2025-1695 - NGINX Unit Java Module Vulnerability Could Trigger CPU Spikes and Limited DoS
Published: June 2024
Severity: Medium
Affected Product: NGINX Unit (Java Language Module)
Versions Impacted: Before 1.34.2
In this post, we'll dig
CVE-2025-27221 - How Ruby’s URI Gem Leaks Authentication Credentials—Vulnerability Details, Exploit, and Fixes
In early 2025, a critical vulnerability was discovered in the widely-used URI gem for Ruby, listed as CVE-2025-27221. This issue affects all versions before 1.
CVE-2025-0555 - How a Simple XSS in GitLab-EE Can Give Attackers Control
The world of cybersecurity is always on the move. In early 2025, a severe Cross-Site Scripting (XSS) vulnerability hit GitLab Enterprise Edition (GitLab-EE), tracked as
CVE-2025-21424 - Memory Corruption in NPU Driver API under Concurrent Access
In early 2025, a new vulnerability was found in some devices using Neural Processing Unit (NPU) drivers. This weakness was cataloged as CVE-2025-21424. At its
Episode
00:00:00
00:00:00