CVE-2023-4513 - How a Wireshark Bluetooth SDP Memory Leak Becomes a Denial of Service Threat
Wireshark is a trusted tool for network analysis, but sometimes, even the best software has vulnerabilities. One such example is CVE-2023-4513, a memory leak in
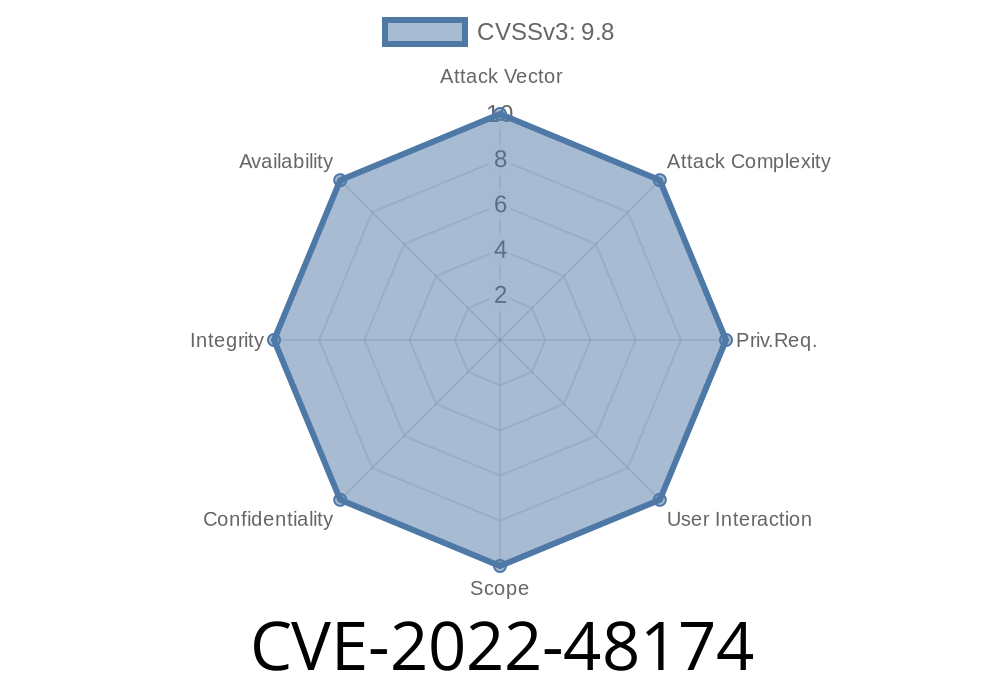
CVE-2022-48174 - Stack Overflow in BusyBox’s ash.c Allows Remote Code Execution in Internet of Vehicles
BusyBox is a popular software suite providing several Unix utilities in a single executable, often referred to as the “Swiss Army Knife of Embedded Linux.
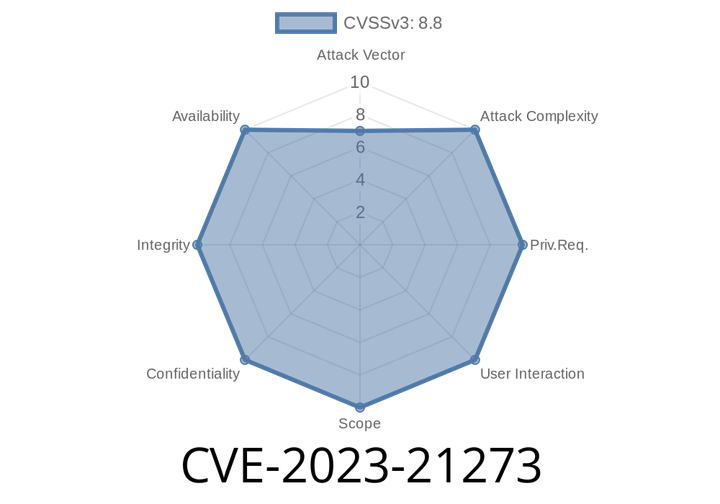
CVE-2023-21273 - Out-of-Bounds Write in SDP_AddAttribute – How This Bluetooth Vulnerability Enables Remote Code Execution
Bluetooth is a technology we use every day, but under the hood, it’s a complex software stack that sometimes hides dangerous vulnerabilities. In this
CVE-2023-40283 - Unpacking the L2CAP Bluetooth Use-After-Free Vulnerability in Linux (with Exploit Insight)
Bluetooth is everywhere, and so is Linux. When a bug creeps into the Linux Bluetooth stack, it’s a big deal for anyone with a
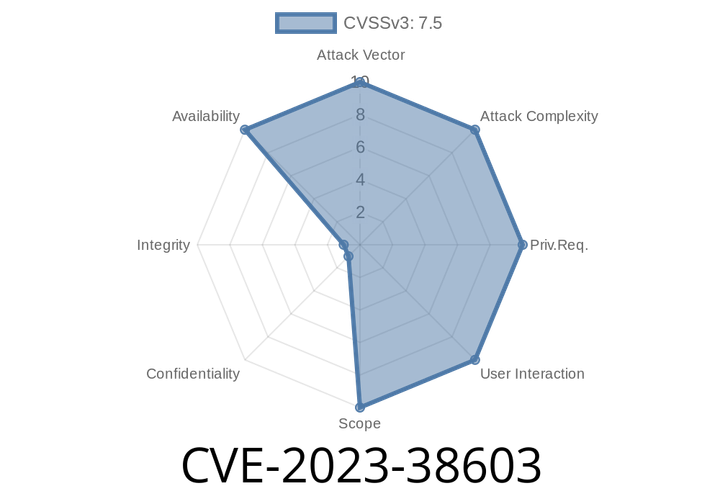
CVE-2023-38603 - How a Simple Bug Could Take Down Your Apple Device — Full Details and Exploit
Apple’s devices are known for their solid security but, like all software, they’re never truly perfect. Every year, researchers and attackers find bugs
Episode
00:00:00
00:00:00