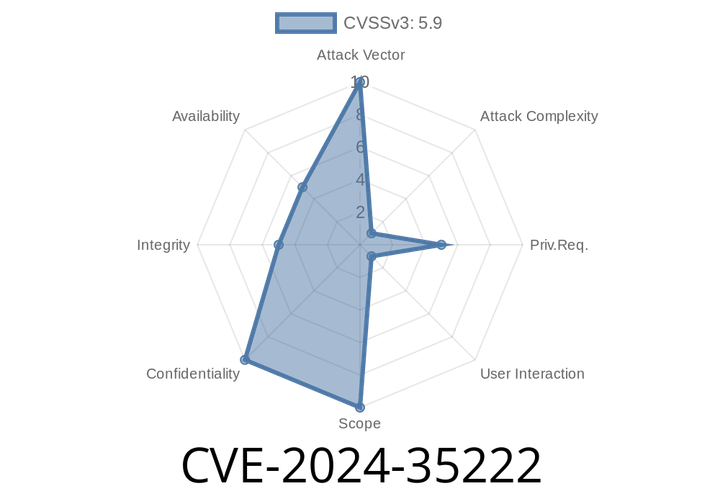
CVE-2024-35222 - How Remote iFrames Could Hijack Your Tauri Apps Until v1.6.7 & v2..-beta.19
Tauri is a popular open-source framework for building secure, cross-platform desktop apps using web technologies — like JavaScript, HTML, and CSS. But recently, a security vulnerability
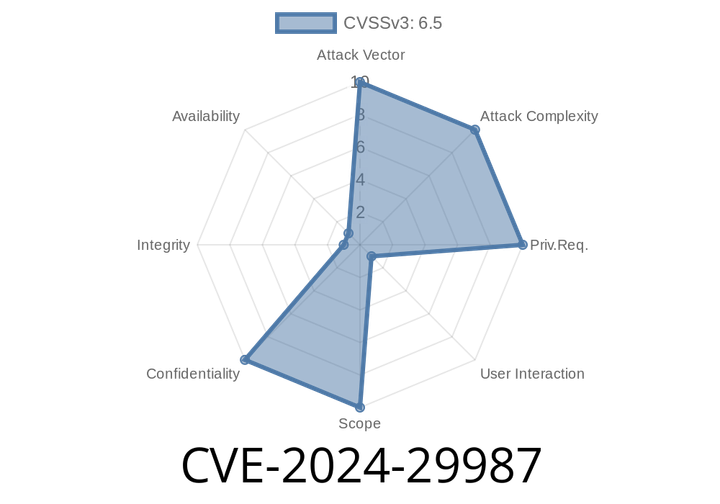
CVE-2024-29987 - Breaking Down the Microsoft Edge (Chromium-based) Information Disclosure Vulnerability
In April 2024, an important vulnerability called CVE-2024-29987 was disclosed, affecting Microsoft Edge (Chromium-based). This security flaw is categorized as an information disclosure vulnerability. While
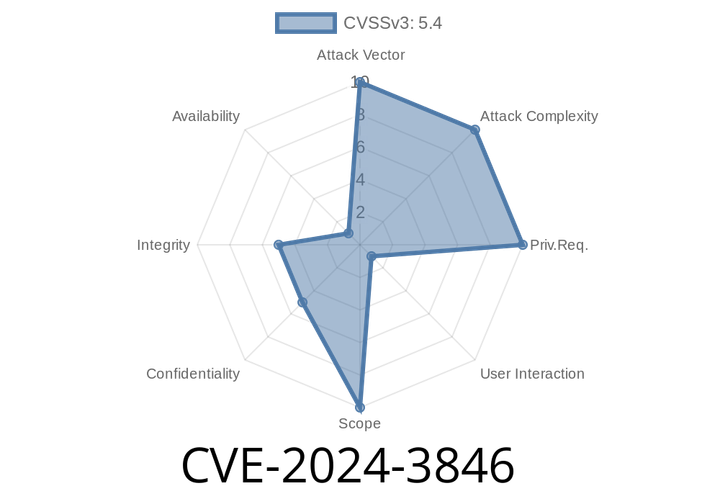
CVE-2024-3846 - How a UI Spoofing Flaw in Google Chrome's Prompts Opened the Door to Trickery
In April 2024, a low-severity security flaw, tracked as CVE-2024-3846, was reported in Google Chrome. While it might not cause mass panic, the vulnerability is
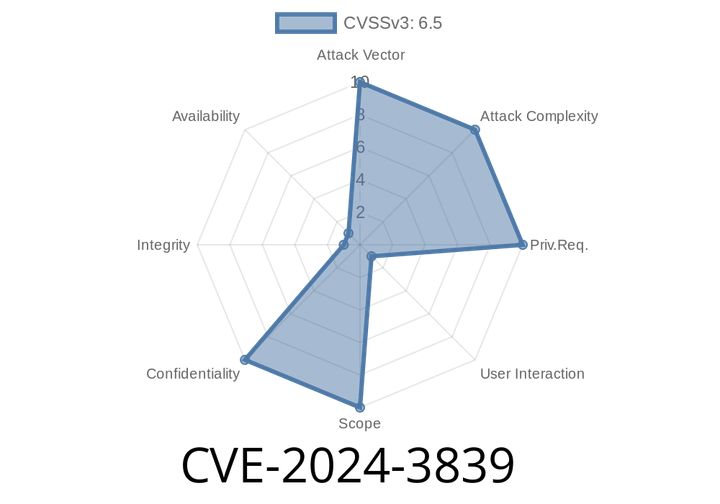
CVE-2024-3839 - Out-of-Bounds Read in Chrome Fonts — How It Leaks Private Data via Crafted HTML
---
What Is CVE-2024-3839?
CVE-2024-3839 is a security vulnerability found in Google Chrome's Fonts handling before version 124..6367.60. Due to an
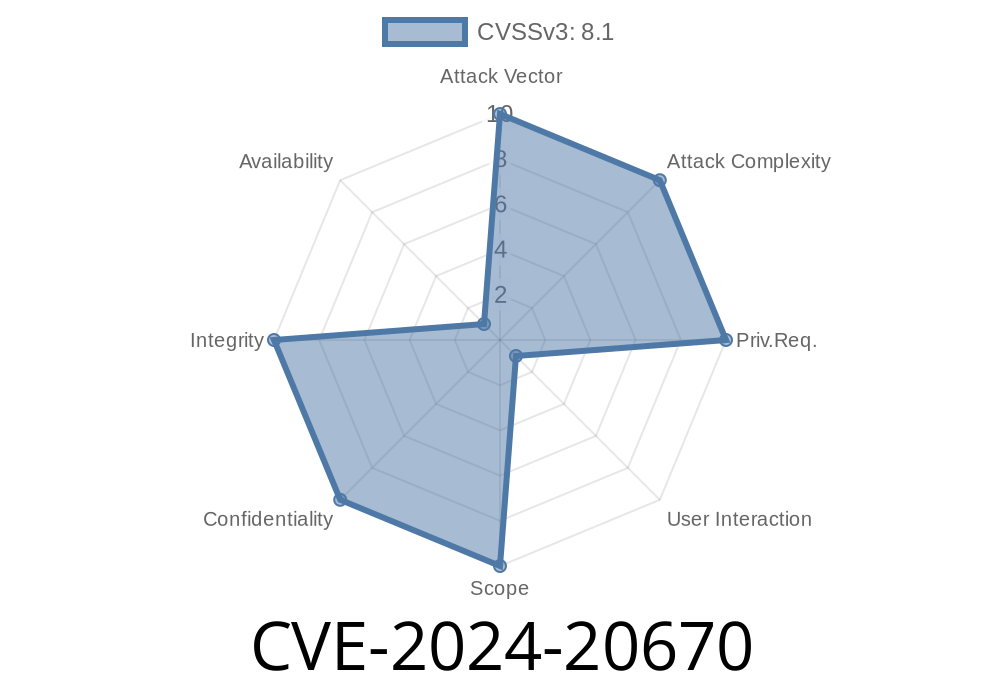
CVE-2024-20670 - Exploiting the Outlook for Windows Spoofing Vulnerability
In January 2024, Microsoft addressed a serious flaw in Outlook for Windows—CVE-2024-20670, a spoofing vulnerability that can let attackers trick users and compromise sensitive
Episode
00:00:00
00:00:00