CVE-2023-27953 - How A Memory Handling Bug in Apple macOS Opened the Door for Remote Kernel Attacks
If you’re using a Mac, keeping your machine updated is always vital—not just for new features, but also to protect your data from
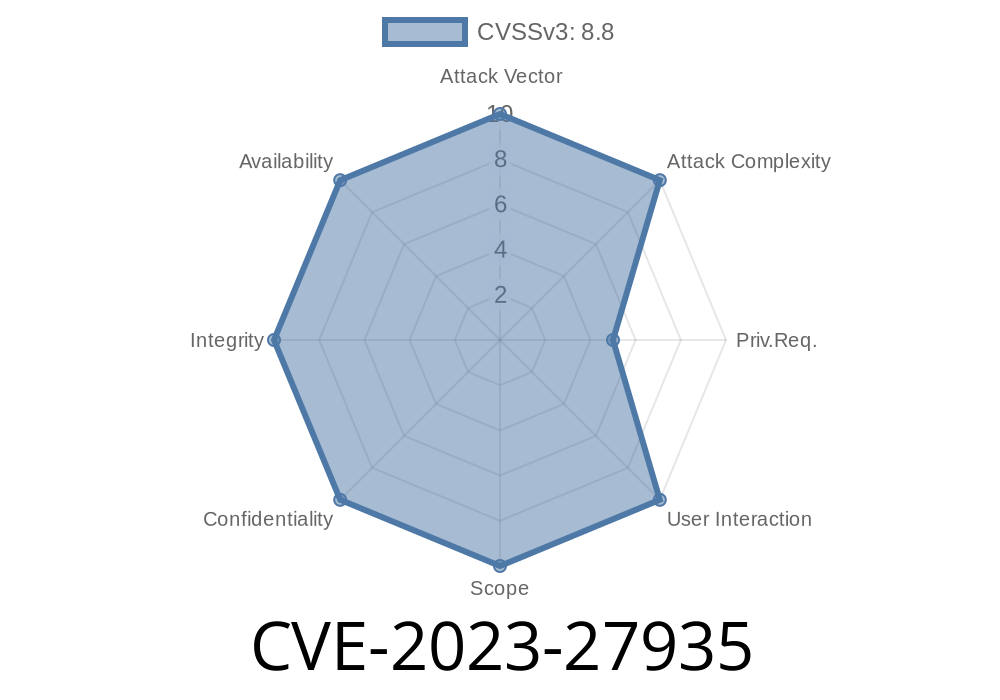
CVE-2023-27935 - How a Remote User Could Crash or Hack Your Mac with a Simple Exploit
Security flaws in operating systems can have major consequences—especially when a remote hacker can exploit them before you patch your system. In March 2023,
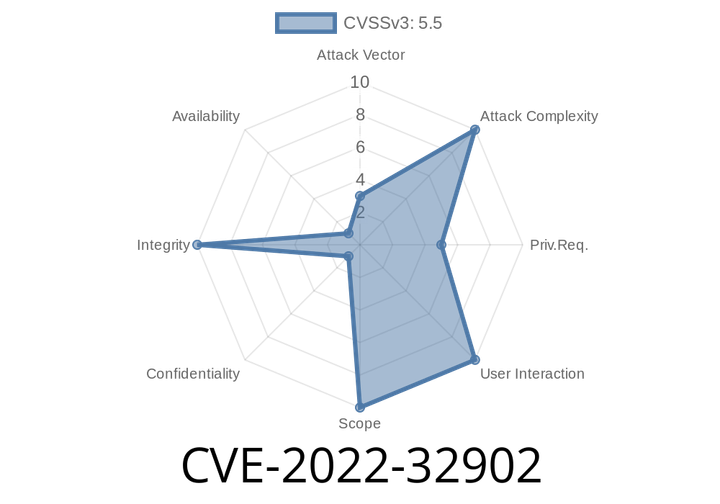
CVE-2022-32902 - How a Logic Flaw Let Apps Bypass Privacy Preferences on Macs
In 2022, Apple patched a significant privacy vulnerability affecting all modern macOS versions (Big Sur, Monterey, Ventura). Dubbed CVE-2022-32902, this bug allowed rogue applications to
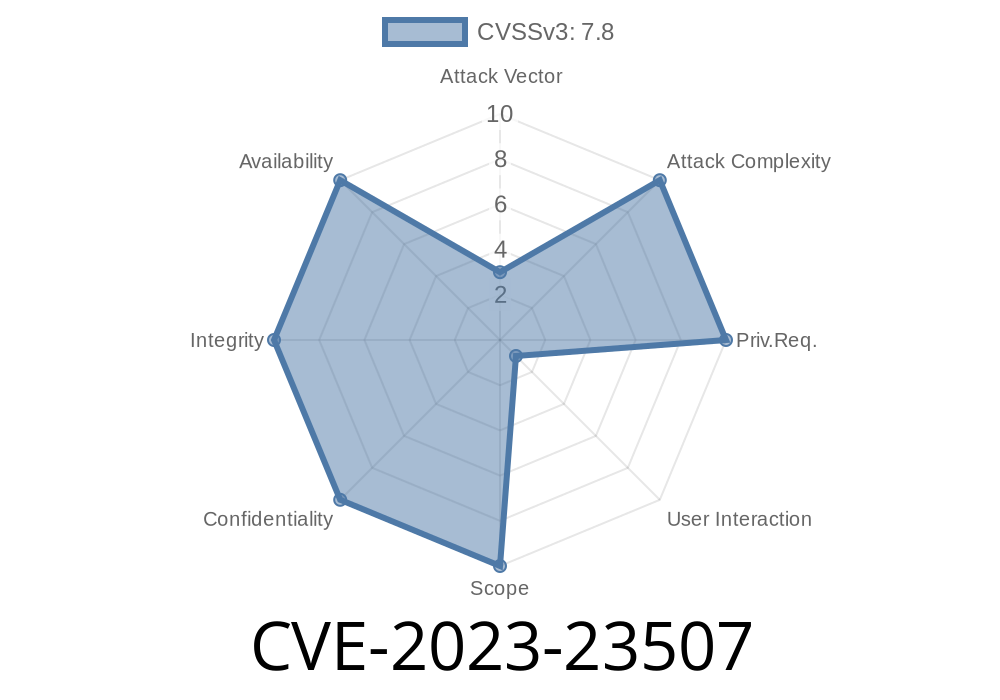
CVE-2023-23507 - Exploiting a Kernel Privilege Vulnerability on macOS (Patched in Ventura 13.2 & Monterey 12.6.3)
---
Introduction
In January 2023, Apple addressed a severe vulnerability tracked as CVE-2023-23507. This issue allowed malicious applications to execute arbitrary code with kernel privileges,
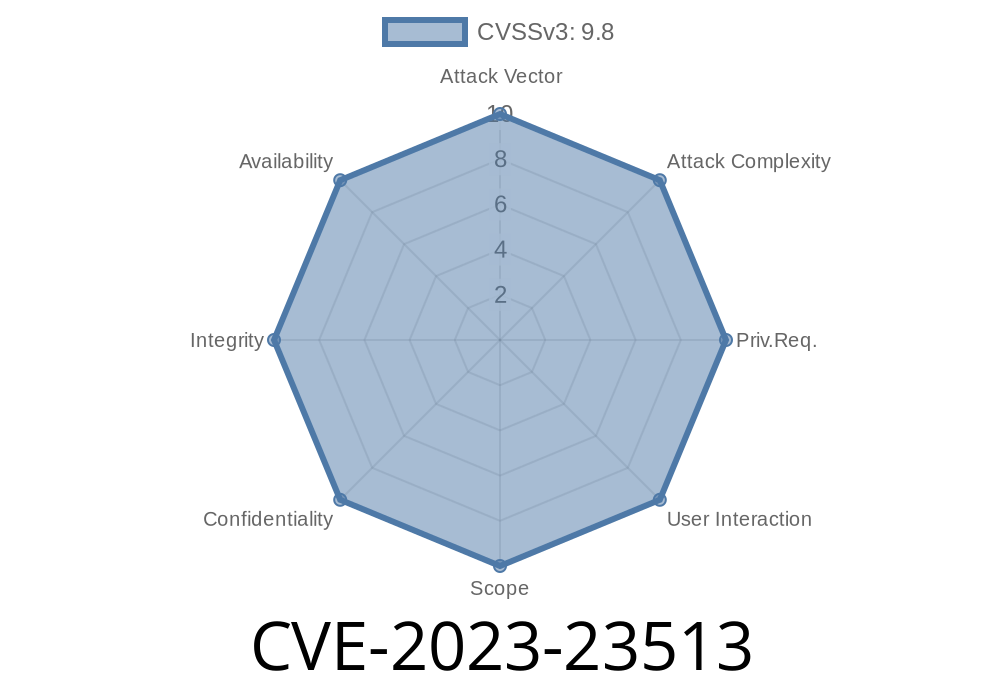
CVE-2023-23513 - Buffer Overflow in macOS Samba Network Share – How Attackers Could Take Over Your Mac
A serious security flaw, CVE-2023-23513, was discovered in macOS relating to how it handles Samba network shares. This vulnerability could let hackers run any code
Episode
00:00:00
00:00:00