CVE-2024-21381 - Microsoft Azure Active Directory B2C Spoofing Vulnerability - Full Analysis and Exploit Details
Azure Active Directory (Azure AD) B2C is widely used for managing customer identities. But in early 2024, a major security issue—CVE-2024-21381—was discovered, allowing
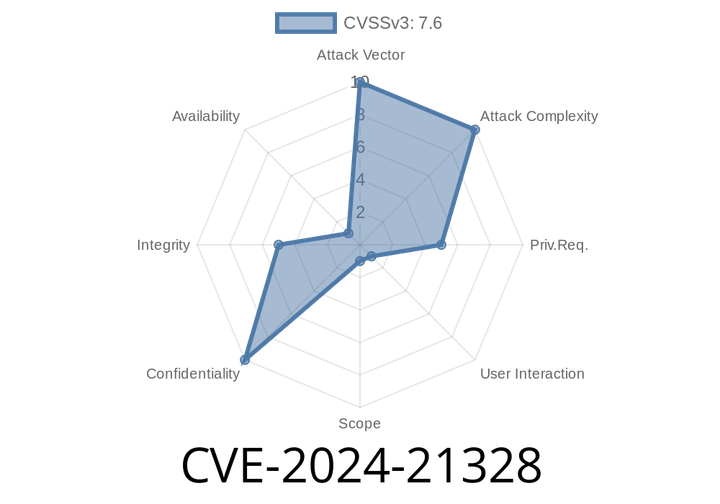
CVE-2024-21328 - Unpacking the Dynamics 365 Sales Spoofing Vulnerability
Microsoft Dynamics 365 Sales is a powerful CRM tool, but in early 2024, security researchers uncovered a serious vulnerability—CVE-2024-21328—that could let attackers impersonate
CVE-2023-6291 - How a Simple Redirect URI Flaw in Keycloak Can Lead to Major Security Breaches
Keycloak is a popular open-source identity and access management solution. It’s used by many organizations to secure applications with Single Sign-On (SSO), manage users,
CVE-2023-2585 - How Keycloak’s Device Authorization Flaw Could Let Attackers Trick OAuth Admins (With Exploit Walkthrough)
Keycloak is one of today’s most relied-upon open source identity and access management (IAM) solutions. If you use OAuth in your organization, there’s
CVE-2023-2422 - How Keycloak’s mTLS Flaw Lets Attackers Impersonate Any Client
Keycloak is an open source identity and access management tool used widely to secure modern applications. In April 2023, a serious security vulnerability was discovered
Episode
00:00:00
00:00:00