CVE-2023-42820 - How an Exposed Random Seed in JumpServer Could Let Attackers Reset Your Password
---
Overview
CVE-2023-42820 is a security vulnerability that affects JumpServer, a popular open source bastion host. This issue comes down to weak handling of random
CVE-2022-4137 - Understanding the Keycloak OAuth 'oob' Endpoint Reflected XSS Vulnerability
---
Introduction
In the world of application security, Cross-Site Scripting (XSS) issues remain a persistent and dangerous problem. One such flaw, tracked as CVE-2022-4137, was
CVE-2023-39531 - OAuth Token Exchange Vulnerability in Sentry Explained
Sentry is a popular platform for tracking errors and monitoring application performance. But in its journey from version 10.. through 23.7.1, a critical
CVE-2023-39261 - How JetBrains IntelliJ IDEA’s Space Plugin Leaked More Than You Think
JetBrains IntelliJ IDEA is the go-to IDE for millions of Java developers. With its wide range of plugins, integrating platforms like JetBrains Space becomes a
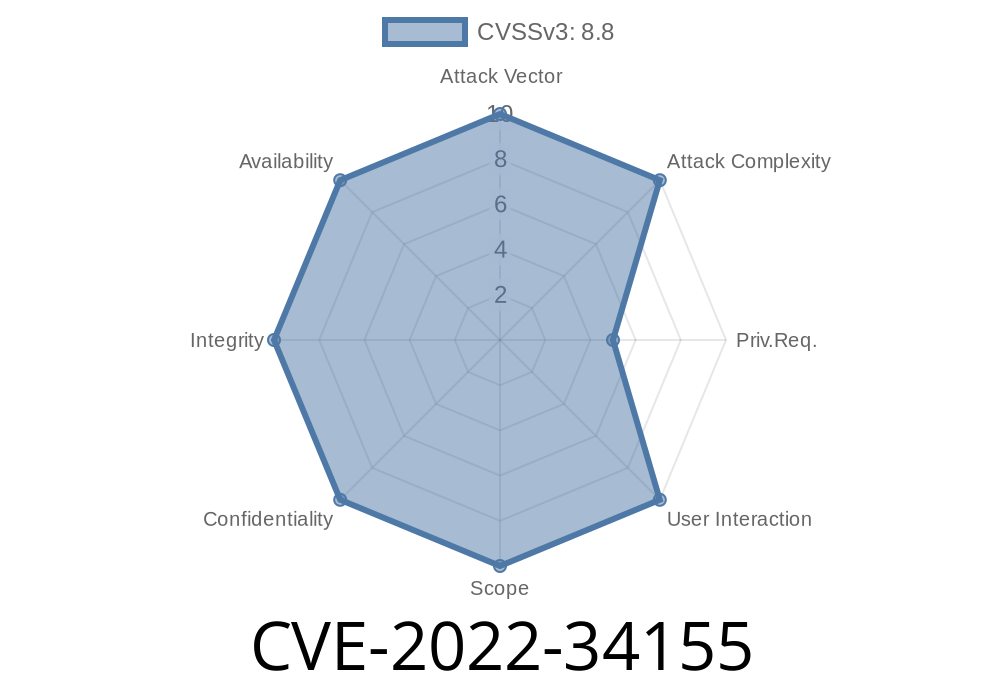
CVE-2022-34155 - Exploiting Improper Authentication in miniOrange OAuth Single Sign On – SSO (OAuth Client) (<= 6.23.3)
In 2022, a serious vulnerability was found in the popular miniOrange OAuth Single Sign On – SSO (OAuth Client) plugin for WordPress. This plugin is widely
Episode
00:00:00
00:00:00