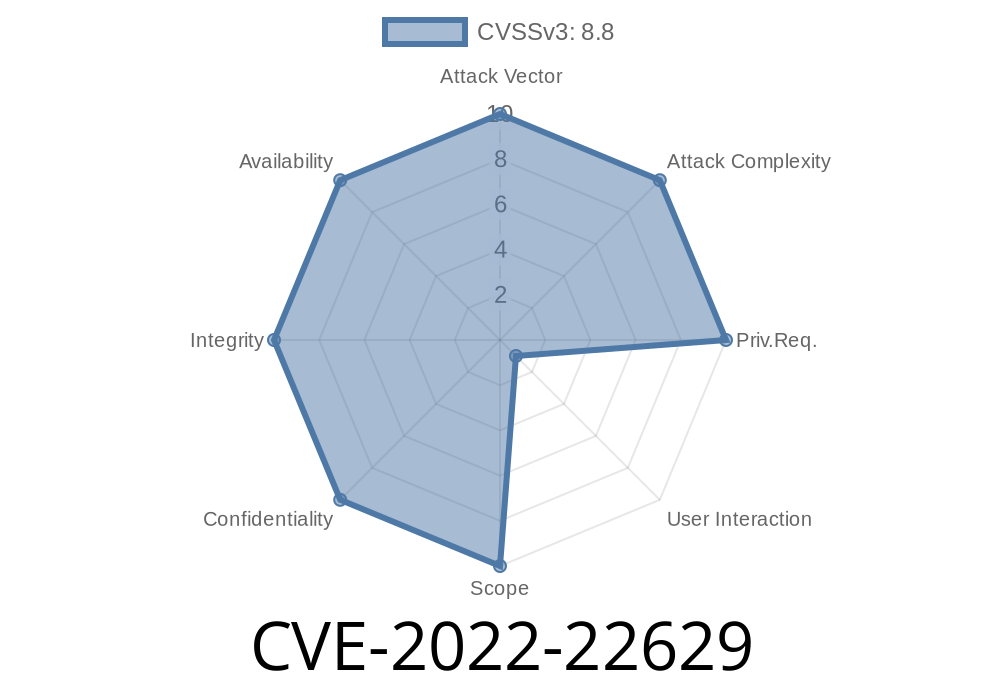
CVE-2022-22629 A buffer overflow was fixed in Monterey 12.3, Safari 15.4, watchOS 8.5, iTunes 12.12.3, iOS 15.4, and iPadOS 15.4.
This issue is fixed in macOS Mojave 10.14.5, Safari 12.5, watchOS 5.2, iTunes 12.12.2 for Windows, iOS 15.3,
CVE-2022-26700 - Unpacking Apple’s Memory Corruption Flaw and How It Was Exploited
In May 2022, Apple patched a dangerous vulnerability tracked as CVE-2022-26700 that lurked in many of its most popular platforms: tvOS, watchOS, iOS, iPadOS, macOS
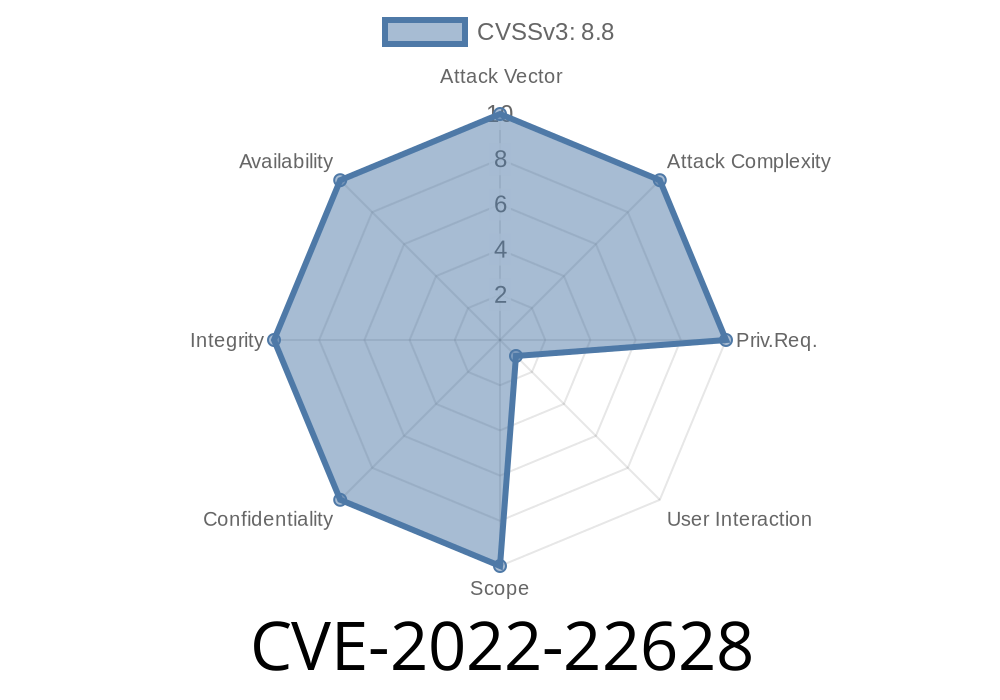
CVE-2022-22628 - A Deep Dive into the Use-After-Free Bug in Apple WebKit
In early 2022, Apple quietly patched a critical security vulnerability—CVE-2022-22628—that affects their WebKit engine. If you use Safari, or any Apple device for
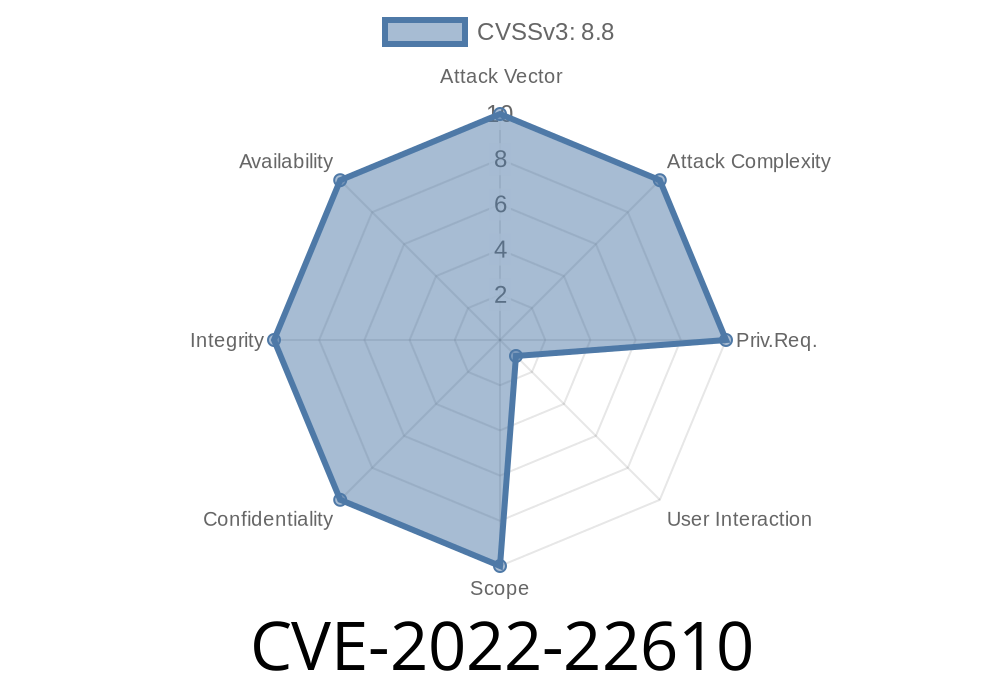
CVE-2022-22610 - How a Memory Corruption Bug in WebKit Put Apple Users at Risk
CVE-2022-22610 might not sound like a major headline, but for millions of Apple users, this security flaw had the potential to become a digital disaster.
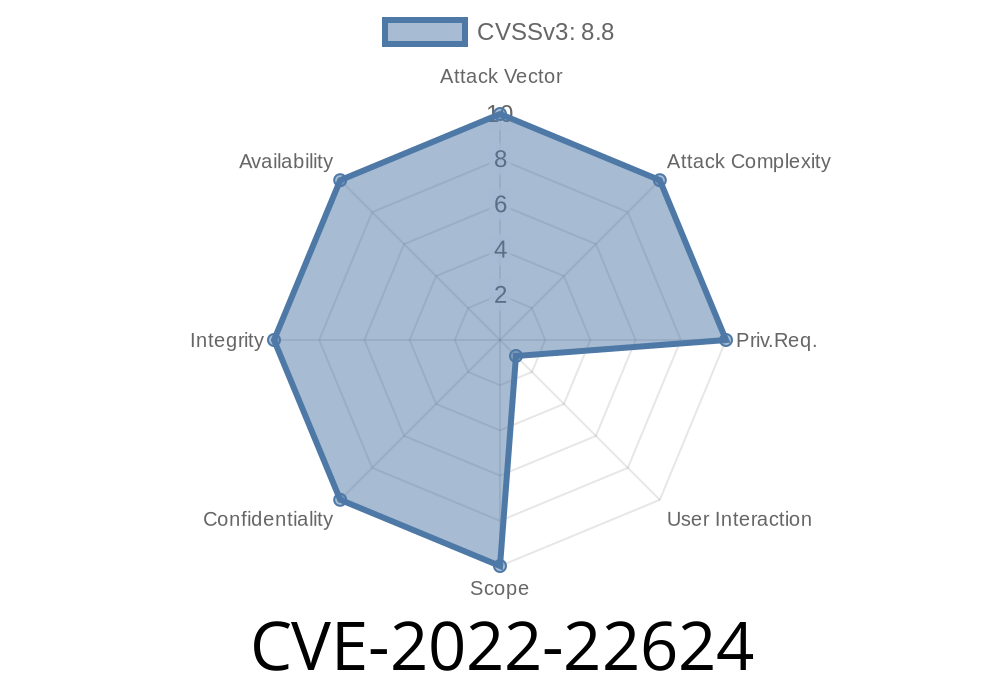
CVE-2022-22624 - A Deep Dive into the macOS, iOS, and Safari Use-After-Free Vulnerability
In early 2022, Apple issued patches for a critical WebKit vulnerability tracked as CVE-2022-22624. This flaw impacted multiple Apple platforms and had the potential for
Episode
00:00:00
00:00:00